Hi folks,its been a long time since I have posted some thing technical,so I will be writing about the challenge I got at NIT KU, where I reverse engineered WinRAR 3.80 using a disassembler and will tell you the same here. Furthermore, major software are analysed using the same way,but just get a bit complex in the methodology. This tutorial is intended for those who are new to reverse engineering and disassembling.
KU, where I reverse engineered WinRAR 3.80 using a disassembler and will tell you the same here. Furthermore, major software are analysed using the same way,but just get a bit complex in the methodology. This tutorial is intended for those who are new to reverse engineering and disassembling.
To perform this hack you will be needing -
How to Reverse Engineer?
You need to have a bit knowledge of assembly language,and in case you don't have it,just cram the steps and it will work anytime,every time. Download the latest version of WinRAR from their website and install it.
I will be cracking Winrar 3.80 here (cuz I already have it:P ). This is basically a 2 step process ( 4 step ,if you want to do things with a professional touch,period) .
Now copy the WinRAR.exe file to desktop. Make a copy of it there.
Step 1 – Hunting for Memory Address
Now load Hackers Disasembler and load the copy in it.
The Disassembler will disassemble the executable in assembly code. Now you need to search for strings that are used in WinRAR program. Press Ctrl + F and type “evaluation” without quotes and search in the assembly code. Hit enter..
After you have reached this block of code by searching, just look at the block of code above it. There you will find that some assembly values are being compared and then code is jumped to some other function. Now see carefully, the “evaluation copy” function must be invoked after some specific condition is met. We need to look for it at the code and the make certain changes to the condition so that the program doesn't checks for the condition.
In the above code you can see this code -
Note : For any WinRAR version, this code and memory address might be different,but the JNE will be same. Just note down the respective memory address that checks.
Now you need to search for the code that brings that ugly nag screen “Please purchase WinRAR license” after your trial period of 40 days is over. For this,look over your toolbar and click on “D” which stands for looking for Dialog references.
Now in the dialog box that opens,search for “please” and you will get the reference as -
Double click on it and you will reach the subsequent code.
The code will be something like
Note : For any WinRAR version, this code and memory address might be different.But the Reminder Memory address code will always PUSH something. Just note down the respective memory address that PUSH ‘s.
Step 2 – Fixing and Patching
Now in this step we will be patching up values of memory addresses we noted earlier. I will be doing this using HVIEW.
Now load the copy you disassembled in Hacker’s Disassembler in Hview.
After you have loaded it, you will see the code is unreadable. Its just like opening an EXE file in notepad. You need to decode it. To do that, just press F4 and yoiu will get an option to decode it. Hit DECODE and you will be able to see code in the form of assembly code and memory addresses.
After you have done that, you need to search for memory addresses you noted down earlier. Just hit F5 and a search box will be there. Now you need to enter the memory address. To do that, enter a “.” and the type memory address neglecting the earlier “00” . The “.” will suffice for “00”. ie -
and search in the code.
After you have reached the respective code, you need to make changes to it. Press F3 and you will be able to edit the code.Now make the following changes -

After you have done it, save it by pressing F9.
Now search for next memory location by pressing F5 and entering it. Reach there and make the following changes by pressing F3 -
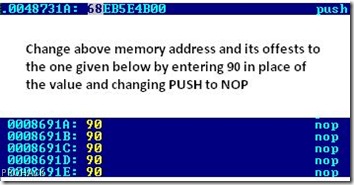
Save the changes by pressing F9 and exit HVIEW by pressing F10.
Congrats..You have cracked WinRAR :) Replace the original WinRAR.exe with this copyofwinrar.exe by renaming it. It will work 100% fine :P
Step 3 – Spicing up the EXE
Now U have a 100% working version of EXE, you might want to change your registration information in WinRAR. TO do this, you can use Resource hacker.

Launch Resource Hacker, load the copyofwinrar.exe in it
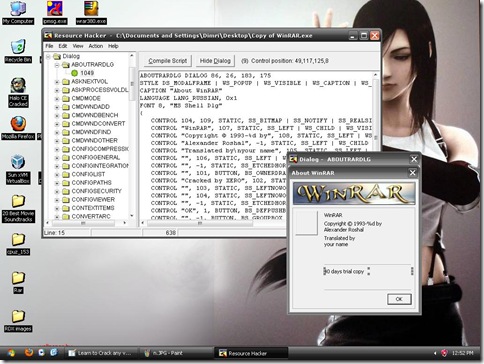
Now go to DIALOG –> Expand tree –> ABOUTRARDLG and click it. Now Find Trial copy line and replace it with your favorite one :P
and click on Compile Script button.

Now save the file with any name on your desktop or any location what so ever.

Now you have a fully patched WinRAR.exe file :)) . If you want to learn that, move on to next step.
Step 4 – Creating a working Patch (or giving Professional touch :P )
I will be using diablo2oo2's Universal Patcher (UPE) for creating the patch. The patch will work like any authentic one for that WinRAR version. Just like the one U downloaded at anytime of your life from any Crack and Keygen website.
Launch Patch Creator and click on add new project. Enter project Information and click on save.

Click on Add – ; Offset patch

After you have done that, double click on offset patch and then

Now in the next window, click on Create Patch and save it. The Patch will be created. Now copy it in WinRAR installation directory and hit on patch, it WILL work.
Congrats you have created a patch of your own and have learned to reverse engineer WinRAR :)
You can crack other software in the same way…just practice,debug and disassemble and you will get the way :)
 KU, where I reverse engineered WinRAR 3.80 using a disassembler and will tell you the same here. Furthermore, major software are analysed using the same way,but just get a bit complex in the methodology. This tutorial is intended for those who are new to reverse engineering and disassembling.
KU, where I reverse engineered WinRAR 3.80 using a disassembler and will tell you the same here. Furthermore, major software are analysed using the same way,but just get a bit complex in the methodology. This tutorial is intended for those who are new to reverse engineering and disassembling.The Tools
Disclaimer – By Reading this tutorial You agree that this tutorial is intended for educational purposes only and the author can not be held liable for any kind of damages done whatsoever to your machine, or damages caused by some other,creative application of this tutorial.
In any case you disagree with the above statement,stop here.
To perform this hack you will be needing -
- Any De-assembler (I use Hackers Disassembler and Hview )
- Resource Hacker
- A patch Creator ( Use Universal Patch Creator or Code fusion)
How to Reverse Engineer?
You need to have a bit knowledge of assembly language,and in case you don't have it,just cram the steps and it will work anytime,every time. Download the latest version of WinRAR from their website and install it.
I will be cracking Winrar 3.80 here (cuz I already have it:P ). This is basically a 2 step process ( 4 step ,if you want to do things with a professional touch,period) .
Now copy the WinRAR.exe file to desktop. Make a copy of it there.
Step 1 – Hunting for Memory Address
Now load Hackers Disasembler and load the copy in it.
The Disassembler will disassemble the executable in assembly code. Now you need to search for strings that are used in WinRAR program. Press Ctrl + F and type “evaluation” without quotes and search in the assembly code. Hit enter..
After you have reached this block of code by searching, just look at the block of code above it. There you will find that some assembly values are being compared and then code is jumped to some other function. Now see carefully, the “evaluation copy” function must be invoked after some specific condition is met. We need to look for it at the code and the make certain changes to the condition so that the program doesn't checks for the condition.
In the above code you can see this code -
00444B6A: 803DF4B84B0000 cmp byte ptr [004BB8F4], 00This is the code responsible for validating you as a legal user :) . Just note down the memory address that leads to jump (JNE) at some memory location. In this case, note down 00444B71 .
00444B71: 0F859B000000 JNE 00444C12
Note : For any WinRAR version, this code and memory address might be different,but the JNE will be same. Just note down the respective memory address that checks.
Now you need to search for the code that brings that ugly nag screen “Please purchase WinRAR license” after your trial period of 40 days is over. For this,look over your toolbar and click on “D” which stands for looking for Dialog references.
Now in the dialog box that opens,search for “please” and you will get the reference as -
ID-REMINDER, “Please purchase WinRAR license”
Double click on it and you will reach the subsequent code.
The code will be something like
* String: “REMINDER”Just note the memory address that invokes the REMINDER dialog. In this case its 0048731A. Note it down.
0048731A: 68EB5E4B00 push 004B5EEB
Note : For any WinRAR version, this code and memory address might be different.But the Reminder Memory address code will always PUSH something. Just note down the respective memory address that PUSH ‘s.
Step 2 – Fixing and Patching
Now in this step we will be patching up values of memory addresses we noted earlier. I will be doing this using HVIEW.
Now load the copy you disassembled in Hacker’s Disassembler in Hview.
After you have loaded it, you will see the code is unreadable. Its just like opening an EXE file in notepad. You need to decode it. To do that, just press F4 and yoiu will get an option to decode it. Hit DECODE and you will be able to see code in the form of assembly code and memory addresses.
After you have done that, you need to search for memory addresses you noted down earlier. Just hit F5 and a search box will be there. Now you need to enter the memory address. To do that, enter a “.” and the type memory address neglecting the earlier “00” . The “.” will suffice for “00”. ie -
Type .444B71 in place of 00444B71
and search in the code.
After you have reached the respective code, you need to make changes to it. Press F3 and you will be able to edit the code.Now make the following changes -

After you have done it, save it by pressing F9.
Now search for next memory location by pressing F5 and entering it. Reach there and make the following changes by pressing F3 -

Save the changes by pressing F9 and exit HVIEW by pressing F10.
Congrats..You have cracked WinRAR :) Replace the original WinRAR.exe with this copyofwinrar.exe by renaming it. It will work 100% fine :P
Step 3 – Spicing up the EXE
Now U have a 100% working version of EXE, you might want to change your registration information in WinRAR. TO do this, you can use Resource hacker.

Launch Resource Hacker, load the copyofwinrar.exe in it

Now go to DIALOG –> Expand tree –> ABOUTRARDLG and click it. Now Find Trial copy line and replace it with your favorite one :P
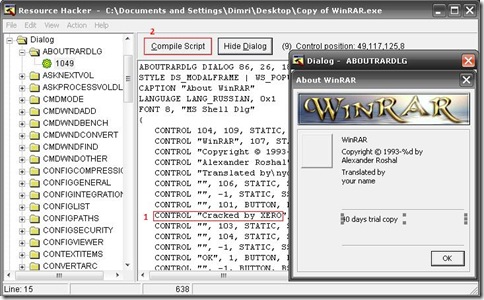 |
and click on Compile Script button.

Now save the file with any name on your desktop or any location what so ever.

Now you have a fully patched WinRAR.exe file :)) . If you want to learn that, move on to next step.
Step 4 – Creating a working Patch (or giving Professional touch :P )
I will be using diablo2oo2's Universal Patcher (UPE) for creating the patch. The patch will work like any authentic one for that WinRAR version. Just like the one U downloaded at anytime of your life from any Crack and Keygen website.
Launch Patch Creator and click on add new project. Enter project Information and click on save.

Click on Add – ; Offset patch

After you have done that, double click on offset patch and then
- Give path of original winrar.exe
- Give path of unmodified Winrar.exe (again)
- Give path for fully patched Winrar.exe (ie Cracked Winrar.exe in this case)
- Click on compare and it will show difference between both files
- Click on save.

Now in the next window, click on Create Patch and save it. The Patch will be created. Now copy it in WinRAR installation directory and hit on patch, it WILL work.
Congrats you have created a patch of your own and have learned to reverse engineer WinRAR :)
You can crack other software in the same way…just practice,debug and disassemble and you will get the way :)
[PS: The above is the long way to do it, I will be telling you the shortest way to crack WinRAR in just 1 step, the main aim of this tutorial was to introduce you to disassemblers and tools, and do some dirty work with your hand. ]